- Part 1: Binary
- Part 2: Hexadecimal
- Part 3: Networking 101 (IP addresses, subnets, etc.)
- Part 4: Scenario based understanding of the 7 layers of the OSI Model
- Part 5: Azure Networking Foundations - VNet, Subnet, Security, and Connectivity
- Part 6: Azure Networking - VMs, IP Addresses, and Load Balancing
- A NIC on a VM can connect to your VNet for example. Properties of a NIC that are normally set in the OS are able to be configured in Azure for your Azure VMs.
- Note: VMs (and all other resources) need to be deployed to the same region as your VNet. So you need a VNet for each region that you have resources.
- A NIC on a VM can also be attached to a load balancer (for highly available applications).
- Up to 250 IPs can be assigned per NIC, and these can be public or private IP addresses.
- You can add/edit IPs by going to your VM resource > Network interface > Settings > IP Configurations > Add. If you select an existing IP address, you can go into another menu where you are able to enable it as Public/Private or assign it as Dynamic/Static. You can also change the actual IP address value for Static IPs. Changing to a new IP address will cause the VM to reboot.
- You can add more NICs to the VM if you need more IPs from a Microsoft block of reserved IP addresses (you cannot port in your own IP address ranges that you are using on prem or otherwise).
- The underlying Azure platform handles connections to/from the machine, you should not RDP into your VM and setup a static IP address for you IPv4 (you will lose access to your machine, it is an unsupported action for an Azure VM and well documented).
- You also should not install a DHCP service on your VM (unsupported as well). You can do dynamic or static IP addresses for your VM.
- Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway.
- MAC address persistence: by default we guarantee that the MAC address will not change for a VM or NIC provided the VM is not deleted, redeployed from disks, or redeployed using the redeploy feature that rebuilds the virtual hardware.
- When you create a new VM you can add it to an existing VNet and subnet. If you want it publicly available, you can add Public IP, or if you don't then select None for the Public IP address (and it will automatically get assigned only a private IP address). You should create a new NSG for it (default option).
IP addresses
- IP addresses are treated as a separate resource in Azure, which allows you to move it from one resource to another.
- Not all resources in Azure support a static (reserved) IP. For example, a VPN Gateway or Application Gateway do not support a static address because they are Microsoft managed resources. The dynamic IP will not change unless you delete or redeploy that resource, however.
- Static (reserved) Public IPs - retain the IP address. The IPs can be moved between services easily and within seconds.
- Public IPv4 resources are a finite resource. You can have 5 public static IP addresses as part of your Azure subscription for no cost, but any additional ones will start becoming a billable resource. Dynamic IPs can help you with cost savings as they are cheaper than static IPs.
Load Balancing
Azure has 4 different options for traffic distribution:
1. Traffic Manager - DNS based

2. Azure Load Balancer - Layer 4 of OSI model (TCP/UDP)
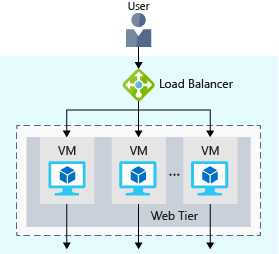
3. Application Gateway - Layer 7 of OSI model (HTTP/HTTPS), can start to add in some Web Application Firewall (WAF), SSL Termination and Cookie based affinity
4. 3rd Party Virtual Appliances - Layer 3-7 of OSI model. Network Virtual Appliances (NVAs) are simply custom IaaS VMs that can provide network functions such as firewall, app firewalls, IDS/IPS, load balancer, and VPN terminators. Azures IP forwarding and UDRs can help send packets to these VMs or override default routing behavior. Many NVAs are available in the Azure Marketplace. Some common vendors are:
1. Traffic Manager - DNS based

2. Azure Load Balancer - Layer 4 of OSI model (TCP/UDP)

3. Application Gateway - Layer 7 of OSI model (HTTP/HTTPS), can start to add in some Web Application Firewall (WAF), SSL Termination and Cookie based affinity
4. 3rd Party Virtual Appliances - Layer 3-7 of OSI model. Network Virtual Appliances (NVAs) are simply custom IaaS VMs that can provide network functions such as firewall, app firewalls, IDS/IPS, load balancer, and VPN terminators. Azures IP forwarding and UDRs can help send packets to these VMs or override default routing behavior. Many NVAs are available in the Azure Marketplace. Some common vendors are:
- Cisco
- Citrix
- F5
- Infoblox
- Check Pint
- Fortinet




